


Secure-IC provide Chip Security Protection IP Cores: Cryptographic algorithm IP such as AES, DES, 3-DES, ECC, RSA, SM2, SM3, SM4, SHA1, SHA2, SHA3, HMAC, countermeasure IP such as TRNG, CTR-DRBG RNG, Digital Sensor, Active Shield, PUF, Smart Monitor, Scrambled Bus, Memory Ciphering, Cyber CPU, Secure Clock, Secure Book, Secure Monitor, Secure JTAG, etc.
• Secure storage without the use of any non volatile memory
• No external key provisioning required
• Does not require costly SRAM blocks
• Proven reliability regarding voltage, temperature and aging with error probability much lower than 10-9
• Trade-off Rebuilding Time vs Entropy manageable by end user
• Security certification ready (including Common Criteria)
• Compliance with ISO/IEC 20897, adapted to CC AVA_VAN.5, FIPS 150-3 lvl 3, OSCCA level 2+
• Possibility to revoke keys (owing to compromission, refurbishing, expiry of a crypto-period)
• Protected against side-channel observation during key extraction using randomization (use of a PRNG)
• Formal security validation (stochastic model)
• Compatible with all process nodes (built from RTL + SDC sources)
• Low weight helper data
• Health tests to attest of the IP proper functioning
• No calibration needed after design, but post-silicon parameters available to make up for inherent fabrication hazards
• Easy integration
• AMBA (APB) interface
A Physically Unclonable Function (PUF) is a security mechanism that uses the inherent physical variations of a device to generate a unique, unclonable output. This output can be used as a cryptographic key or a device identifier. PUFs rely on the fact that the exact physical properties of a device, such as the physical and electrical characteristics on a chip, can never be replicated exactly. This makes PUFs a highly secure method for protecting sensitive information and ensuring device authenticity. PUFs are often used in a wide range of applications, including secure boot, secure storage, and secure key generation. This PQC ready PUF IP Core is compliant with ISO/IEC 20897 where Secure-IC has been the lead party for PUF quality test standard, thus making it the easiest technology to use on the market and the most reliable (with no need to make a testchip before). In addition it can be used in any technology node and foundry.
PUF IP Core is a secret key generation system based on Physically Unclonable Functions (PUF). The secret key is extracted by the PUF from the silicon by using its inherent properties: technological dispersions are amplified into digital signals (bits of information). The key generated by the PUF is not readable but extracted using a group of helper-data. This distinctive feature allows a real protection against the reverse-engineering techniques compared to traditional methods that store the key in non-volatile memory.
PUF IP core ensures the following properties:
• Steadiness
• Randomness• Uniqueness
• Tamper resistance
• Mathematical Unclonability
• Physical unclonability
Security metrics:
• Entropy = 128.0 bit for a typical AES-128 key
• Reliability = fixed to the desired value, e.g., 1 FIT for ASIL D
• Entropy & reliability ensured in all specified corners (owing to adaptive control, a unique feature of our PUF)
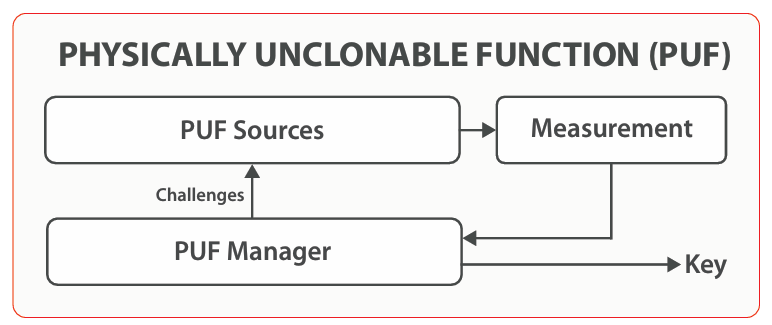
The figure above represents the PUF architecture. The PUF manager controls the PUF sources by giving various challenges. The measurements returned by the PUF sources are processed by the manager to generate the key.
• Secure storage without the use of any non volatile memory
• No external key provisioning required
• Does not require costly SRAM blocks
• Proven reliability regarding voltage, temperature and aging with error probability much lower than 10-9
• Trade-off Rebuilding Time vs Entropy manageable by end user
• Security certification ready (including Common Criteria)
• Compliance with ISO/IEC 20897, adapted to CC AVA_VAN.5, FIPS 150-3 lvl 3, OSCCA level 2+
• Possibility to revoke keys (owing to compromission, refurbishing, expiry of a crypto-period)
• Protected against side-channel observation during key extraction using randomization (use of a PRNG)
• Formal security validation (stochastic model)
• Compatible with all process nodes (built from RTL + SDC sources)
• Low weight helper data
• Health tests to attest of the IP proper functioning
• No calibration needed after design, but post-silicon parameters available to make up for inherent fabrication hazards
• Easy integration
• AMBA (APB) interface
• IoT
• Mobile
• Automotive (Qualified AEC-Q100 grade 0)
• Bank & Payment
Secure-IC is located in France and specializes in the embedded system security, offering security IP cores, security analysis and testing platform, and security consultant services. Including secure encryption algorithms, protection IP authorizations, full range of security analytics test platform. Secure-IC has been into the Chinese market Over the years, a number of vendors and research institutes have chosen Secure-IC platform as a safety testing and research tools, has been a good evaluation. Receiving a good rating.
Secure-IC biggest advantage over competitors is the technology, the most advanced technology by leaps and bounds. Specific products include: encryption algorithms, analysis algorithms, a variety of protection IP, as well as for the actual chip security attack analysis equipment and chip design source code for security simulation analysis software.
With the arrival of the intelligent era, embedded systems as the carrier of the Internet of Things, car networking, artificial intelligence, cloud computing, electronic payment will be more and more into people's lives and greatly improve people's lives. However, with the popularization and application of embedded systems, their security is also threatened more and more. At the present stage, the most advanced threats to embedded system chip are Side Channel Attack, Fault Injection Attack and Hardware Trojans Threaten.
SCA (Side Channel Attack): Using embedded system power, electromagnetic and other leaked information, through statistical mathematical analysis methods such as SPA, CPA, DPA, MIA, CEMA, etc. to break the key of an encryption algorithm;
FIA (Fault Injection Attack): Force the system to generate error feedback by injecting a fault into the encryption system. By analyzing the feedback result, a system security mechanism is cracked. Compared with the side channel analysis, the fault injection analysis method is more complicated and advanced. higher efficiency. Common fault injection methods include laser fault injection, electromagnetic fault injection, voltage glitch fault injection and clock glitch fault injection.
Hardware Trojan Horse is a special module circuit deliberately implanted in a chip or electronic system or a defective module circuit unintentionally left by the designer. Under special condition touch, the module can be used by attackers to achieve purposefulness tampering, or destructive features. Hardware Trojans can cause information leaks, circuit features have been tampered with, and the entire chip is maliciously controlled.
Secure-IC Corporation has developed different security analysis and protection tools to address the threats to embedded system security:
1. Side channel attack and fault injection safety analysis equipment: Secure-IC Analyzr
2. Side channel attacks and fault injection simulation software: Secure-IC Virtualyzr
3. Side channel attacks and fault injection data mining and leakage finder analysis software: Secure-IC Catalyzr
4. Security IP cores: Secure-IC Security IP cores
5. Hardware Trojan detection and protection Hardware Trojan Horse Detection and Defense.
Secure-IC focuses on the development of embedded systems security technology, providing a full set of chip detection and protection devices to protect users from malicious attacks and cyber threats.
Analyzr is a chip security assessment and analysis tools that conducts security attack testing and assessment on actual chips through Side Channel Attack analysis and Fault Injection Attack analysis to locate security vulnerabilities, analyze security leaks and improve security protection.
Analyzr supports SCA: Through the device to capture the measured system during the encryption process of physical leakage information such as power consumption, electromagnetic, etc., through the SPA, CPA, DPA, MIA, TA and other methods to analyze the key to crack the system.
Support classic algorithms AES, DES / 3-DES. RSA, ECC and so on
Support domestic encryption algorithms such as SM2, SM3, SM4 and so on
Analyzr Supports FIA: Injecting faults into the system under test through the device, forcing the system under test to generate error feedback that can be used. By analyzing the feedback results, the FIA can locate security vulnerabilities of the chip under test and crack the system security mechanisms. Users analyze the chip's security threats to improve the corresponding security protection strategy.
Supports all types of active attacks: electromagnetic fault injection, laser fault injection, clock glitch injection, voltage glitch injection, and more.
Side channel information leakage and fault injection threat to the security of the chip is very large, but usually these two aspects of the assessment is on the actual chip or FPGA simulation board. Actual chip production takes time and cost, and FPGA emulation has a large gap with the actual chip. Secure-IC Virtualyzr can solve this problem by evaluating the encryption algorithm directly against the chip design code in the early stages of the design. Injecting security.
Virtualyzr simulates the design's source code (Verilog, VHDL) through digital simulation and modeling without the need for any hardware device (except a powerful computer).
Virtualyzr supports different levels of design code:
RTL,
Post-Synthesis,
Post Place & Route
Virtualyzr supports the development platform and development environment including:
Support Xilinx and development environment ISE, VIVADO
Support Actel / Microsemi and development environment Libero
Support Altera and development environment Quartus
Support ASIC and development tools Cadence / Synopsys
SCA & FIA Data Mining and Leakage finder Software Catalyzr is specifically designed for security analysis to manage big data sets of traces, find leaks and extract information:
• From the evaluation system
• Measure from the side channel
• From the results of the analysis
Catalyzr is a complete data mining tool that helps users select important data and interpret results. Its unique refinement approach allows detection and location of information leaks, navigation, manipulation, and comparison datasets to find critical information and to guide assessors to what should be leaked activity locations. Multidimensional browsing provides a means of analyzing complex data sets for Accelerate safety assessments and share diagnostic results with teams and users. It is crucial to help analysts locate leaks and extract them in time and space.
Catalyzr offers 3 main uses:
1, learn multi-dimensional (XYZ, frequency, voltage, duration ...) Test data under the conditions of measurement
2, detect and find leaks
3, enhance the classic assessment process: rapid analysis of parameters and data processing link
Catalyzr complements the effective analysis of Analyzr and Virtualyzr's assessment process, reducing the magnitude of input data and the time cost of interpreting the results.
At the same time, as an open tool, the platform lets users add custom input and output formats and processing methods.
Secure-IC designed different security IP cores for different security risk loopholes.
Secure-IC sells IP cores based on customer requirements, according to different levels of license for sale, including from the initial step to all the source code to varying degrees.
Secure-IC provide various security IP cores as following list (keep updating).
| AES | Encryption, against Side-Channel Attacks |
| DES / 3-DES | Encryption, against Side-Channel Attacks |
| RSA | Encryption, against Side-Channel Attacks |
| ECC | Encryption, against Side-Channel Attacks |
| HASH (SHA-1/MD-5) | Encryption, against Side-Channel Attacks |
| SM2 | Encryption, against Side-Channel Attacks |
| SM3 | Encryption, against Side-Channel Attacks |
| SM4 | Encryption, against Side-Channel Attacks |
| TRNG | True Random Number Generator,Digital,against Harmonic EM Attacks |
| PUF | Digital, Anti Cloning/Counterfeiting,100% Unique, Random and Steady ID Generation |
| Digital Sensor | Anti Fault Injection Attacks, All-in-one Fault Injection Detector, Entirely Digital |
| Active Shield | Active Protection against Intrusive Attacks on ASIC, Anti Intrusive Hardware Modification. |
| Scrambled BUS | Encrypted Information to Prevent Probing on BUS, Anti Eavesdroping |
| Memory Ciphering | Memory Protection Against Reverse Engineering and Tampering |
| Secure Clock | Anti Synchronization to prevent efficient SCA and FIA |
| Secure JTAG | Authentication System to Secure the debugging channel on chip, Anti JTAG Violation |
| Secure Boot | Maximum security-enabling root-on-trust, Anti Firmware Tampering |
| Secure Monitor | Maximum security-enabling monitoring, Security policy bypass |
| CyberCPU CPU | CPU-agnostic Cyber Attack Sensor |

Current Products:Security IP: PUF