


Secure-IC provide Chip Security Protection IP Cores: Cryptographic algorithm IP such as AES, DES, 3-DES, ECC, RSA, SM2, SM3, SM4, SHA1, SHA2, SHA3, HMAC, countermeasure IP such as TRNG, CTR-DRBG RNG, Digital Sensor, Active Shield, PUF, Smart Monitor, Scrambled Bus, Memory Ciphering, Cyber CPU, Secure Clock, Secure Book, Secure Monitor, Secure JTAG, etc.
Digital,protection against Harmonic EM Attacks
Digital,protection against Harmonic EM Attacks
1. GLOBAL OVERVIEW
True Random Number Generators (TRNGs) are used to generate statistically independent sets of bits for various applications such as One Time Pad cryptography, key generation, seeds for PRNGs, masks to protect an implementation against side-channel analysis.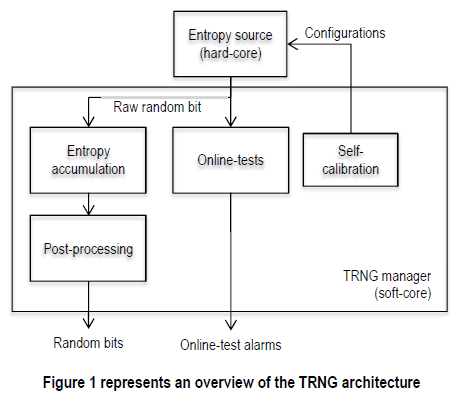
Secure-IC provide various security IP cores as following list (keep updating).
| AES | Encryption, against Side-Channel Attacks |
| DES / 3-DES | Encryption, against Side-Channel Attacks |
| RSA | Encryption, against Side-Channel Attacks |
| ECC | Encryption, against Side-Channel Attacks |
| HASH (SHA-1/MD-5) | Encryption, against Side-Channel Attacks |
| SM2 | Encryption, against Side-Channel Attacks |
| SM3 | Encryption, against Side-Channel Attacks |
| SM4 | Encryption, against Side-Channel Attacks |
| TRNG | True Random Number Generator,Digital,against Harmonic EM Attacks |
| PUF | Digital, Anti Cloning/Counterfeiting,100% Unique, Random and Steady ID Generation |
| Digital Sensor | Anti Fault Injection Attacks, All-in-one Fault Injection Detector, Entirely Digital |
| Active Shield | Active Protection against Intrusive Attacks on ASIC, Anti Intrusive Hardware Modification. |
| Scrambled BUS | Encrypted Information to Prevent Probing on BUS, Anti Eavesdroping |
| Memory Ciphering | Memory Protection Against Reverse Engineering and Tampering |
| Secure Clock | Anti Synchronization to prevent efficient SCA and FIA |
| Secure JTAG | Authentication System to Secure the debugging channel on chip, Anti JTAG Violation |
| Secure Boot | Maximum security-enabling root-on-trust, Anti Firmware Tampering |
| Secure Monitor | Maximum security-enabling monitoring, Security policy bypass |
| CyberCPU CPU | CPU-agnostic Cyber Attack Sensor |

Current Products:Security IP: TRNG